
Vulnerability introduction On January 10th, 2020, ThinkPHP team released a patch update to fix an arbitrary file operation vulnerability caused by unsafe SessionId. This vulnerability allows attackers to create arbitrary files and delete arbitrary files under the condition that the target environment is session-enabled, and in certain cases, they can also get the shell.
The specific affected version is ThinkPHP6.0.0-6.0.1.
Vulnerability reappearance
The local environment is reproduced by ThinkPHP 6.0.1+PHP7.1.20+Apache. Under certain circumstances, you can write a webshell by executing the test verification program, as shown in the following figure:
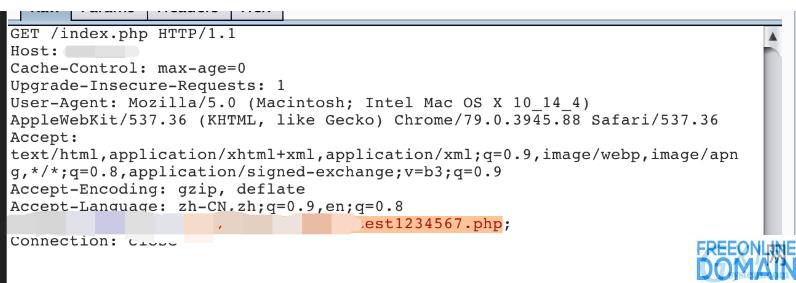
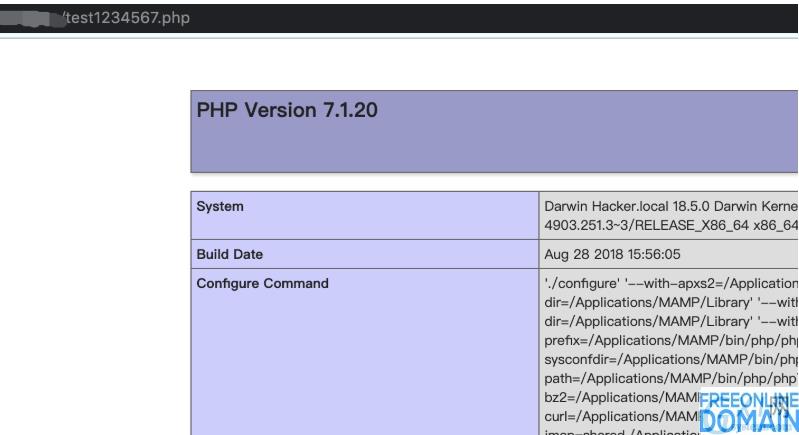
Vulnerability analysis
According to the official github commit:
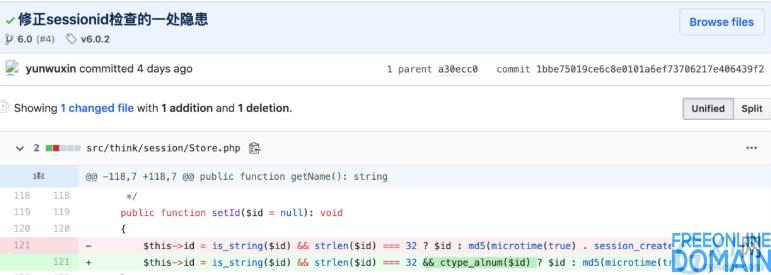
https://github.com/topthink/framework/commit/1bbe75019ce6c8e0101a6ef73706217e406439f2
Therefore, it is speculated that it may be caused by file writing when storing session. Then, trace: vendor/topthink/framework/src/think/session/store.php: 254.
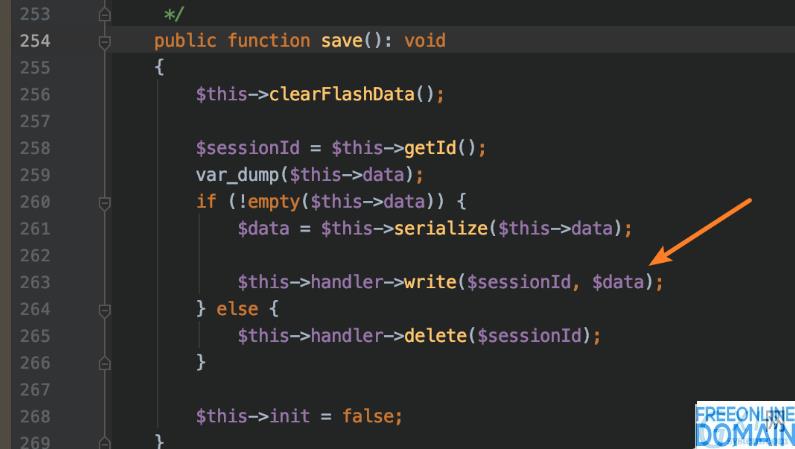
A write function is called here, follow up: vendor/topthink/framework/src/think/session/driver/file.php: 210.
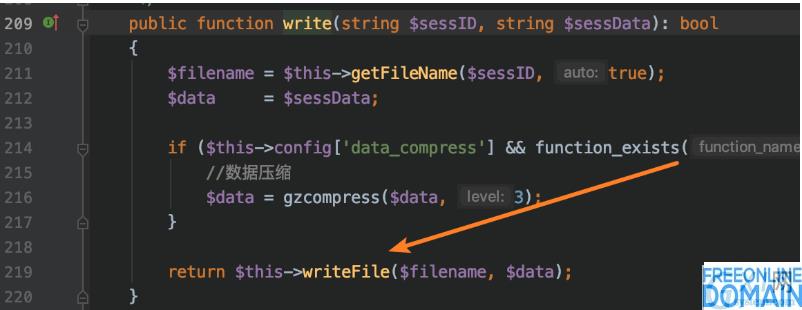
Call the writeFile function, followed by:
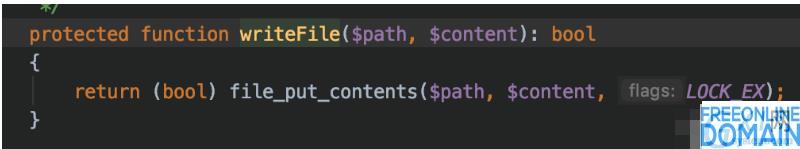
It was an operation to write to a file.
Continue to look backwards to see if the file name is controllable. The file name comes from the value of $sessionId obtained from the initial getId (). Since there is a getId, there will be a setId. Take a look at the function content:
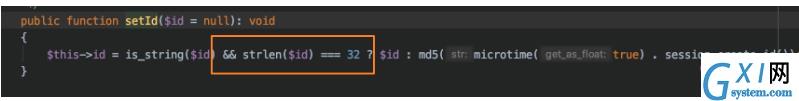
When the passed-in parameter $id meets the length of 32 bits, the value is set to $this->id. Look at the place where setId is called: vendor/topthink/framework/src/think/middleware/sessioninit.php: 46.
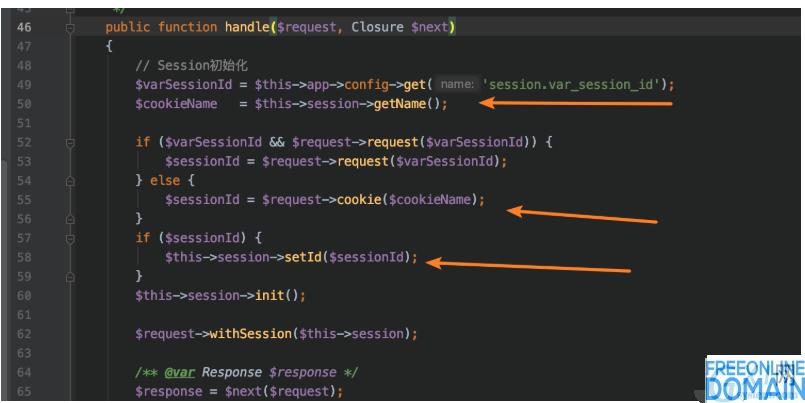
The value of $cookieName here is PHPSESSID.
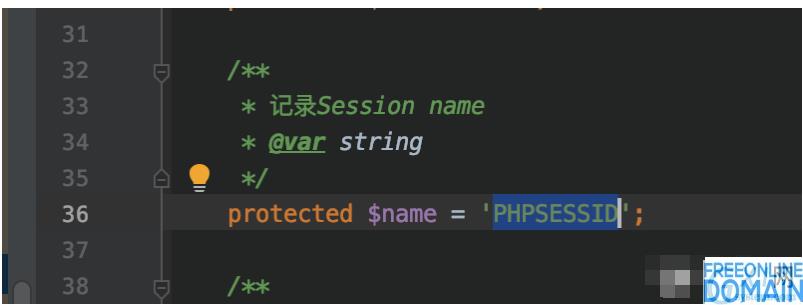
And $sessionId is a value named PHPSESSID in cookie, so it is controllable by attacker, which leads to controllable file name written.
The file name written is controllable, so is the content written controllable? Analysis shows that the content written is the content used to create the session. However, the creation of session is determined by the actual back-end business logic, and no session is created in the default environment. Therefore, arbitrary file writing cannot be done in the default environment.
In the process of in-depth analysis of this vulnerability, we found that this vulnerability can also delete arbitrary files, and file deletion has low dependence on back-end business logic.
Or in vendor/topthink/framework/src/think/session/store.php: 254:
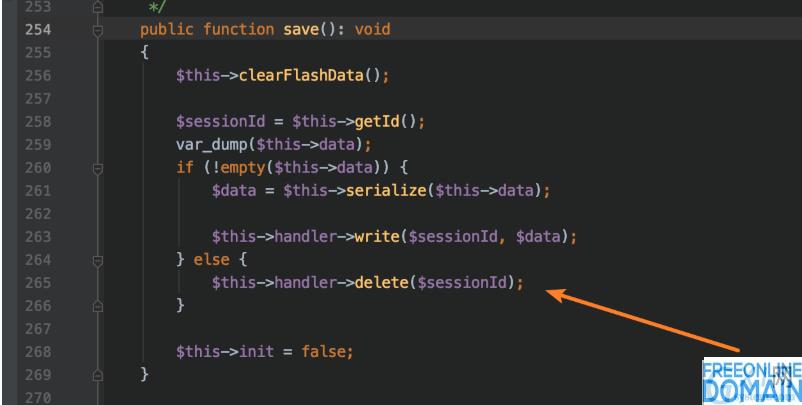
Through analysis and verification, we found that the vulnerability (as shown above) can also cause arbitrary file deletion.
summary
When the target environment is Windows and session is turned on, it is vulnerable to arbitrary file deletion attacks.
Under the condition that the target environment opens the session and the written session is controllable, it is vulnerable to arbitrary file writing attacks.
Relevant users are advised to upgrade to ThinkPHP6.0.2 version 6.0.2 in time to avoid being attacked.
Gxlsystem.com, a lot of free thinkphp introductory tutorials, welcome to learn online!
Copyright Description:No reproduction without permission。

Knowledge sharing community for developers。
Let more developers benefit from it。
Help developers share knowledge through the Internet。
Follow us